CVE-2023-46013 Eramba Community Edition v3.21.1 - Insecure Direct Object Reference (IDOR)
Description
Eramba Community Edition App Version 3.21.1 is vulnerable to an insecure direct object reference (IDOR). This vulnerability allows a low-privileged user to obtain security program artifacts that have been uploaded to the application regardless of the user’s authorization to access those artifacts. This vulnerability can be exploited through the manual manipulation of the artifact’s object identifier in the URL when downloading a program artifact that the user is authorized to access.
Proof-of-Concept
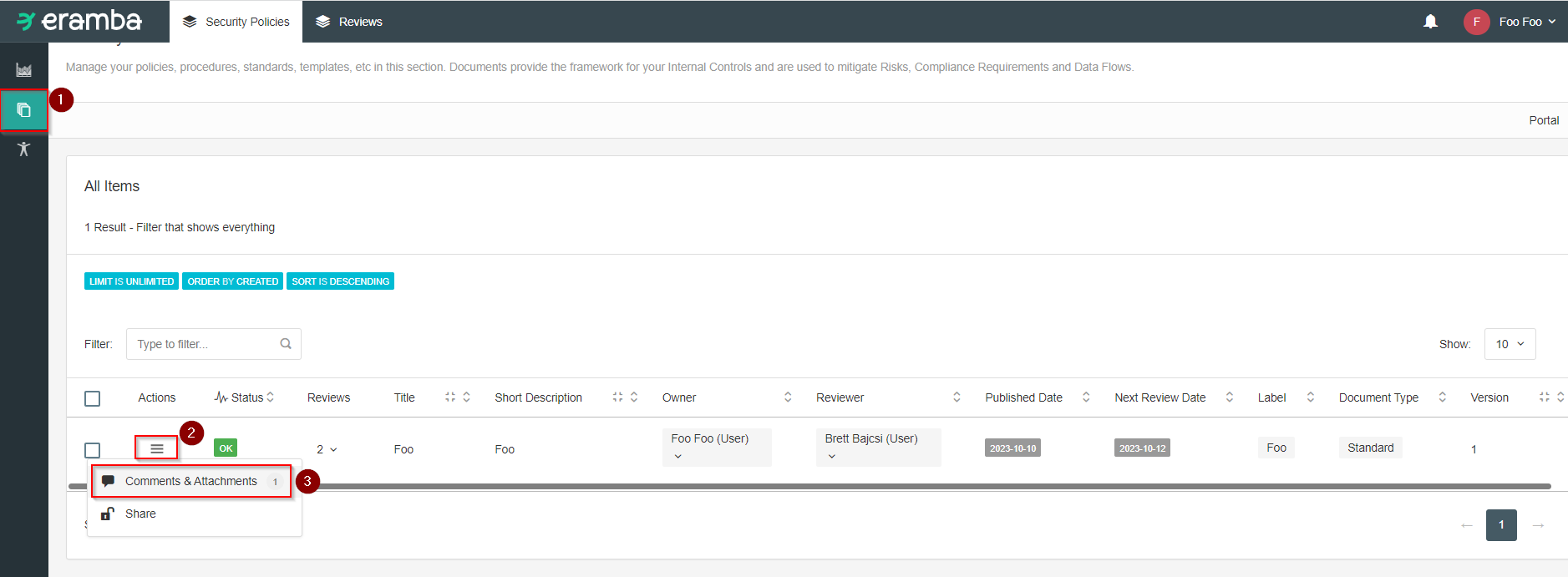
Log into Eramba, navigate to a section of the application that has security program artifact attachments, such as the Security Policies section.
Select the hamburger button then “Comments & Attachments” of a security policy with an artifact attachment you are currently authorized to download.
Add attachment.
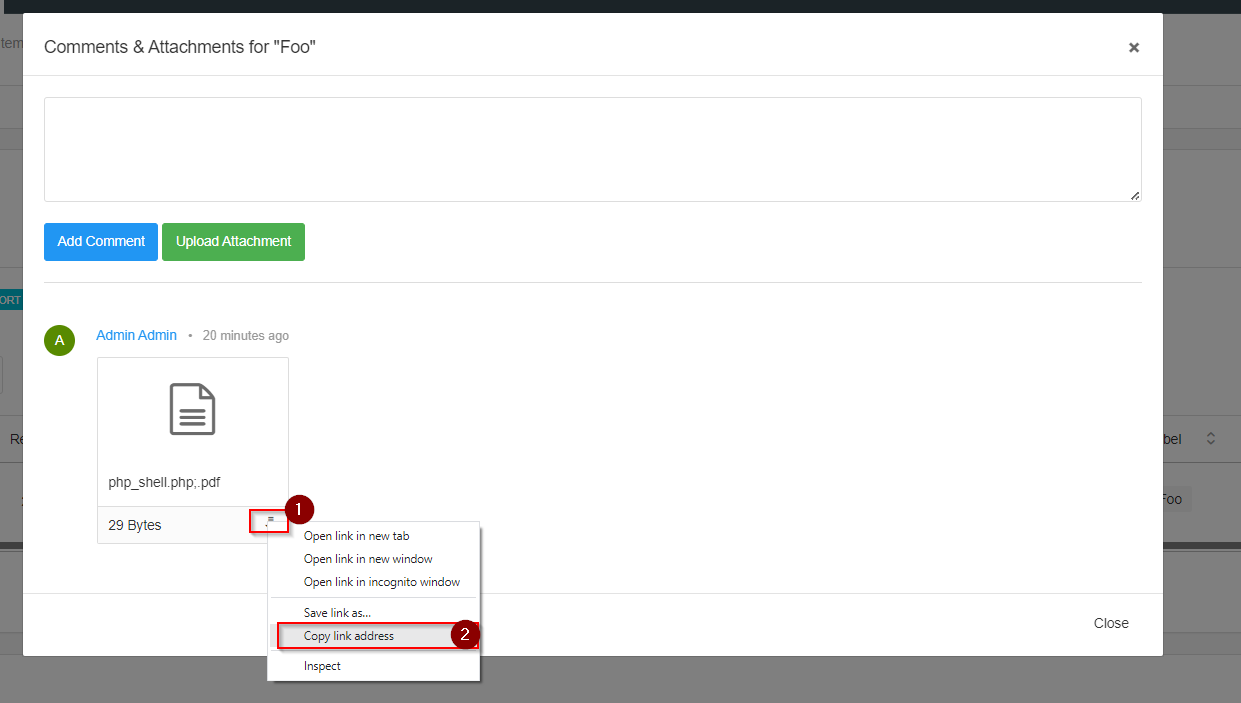
In the pop-out window, right-click on the download icon for the artifact you are authorized to access then select “Copy link address”.
Right click elipses of attachment to copy link address.
In a new browser tab, paste the link to download the authorized artifact and change the identifier, a number value, to that of the number identifier for an artifact you are not authorized to access then hit enter to download the unauthorized artifact.
Attachment with direct object number in URL.
NOTE: enumeration of the artifact attachments your role is authorized for will be required to ensure proper testing of this proof-of-concept. With a large number of attachments, this can be a difficult task.
Mitigation
Users of Eramba Community Edition should upgrade to version 3.22.0 or later. Release 3.22.0
Reference
Vendor Page
CVE Description
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-46013
Timeline
2023-10-11: Vulnerability discovered
2023-10-13: Vendor contacted
2023-10-16: Vendor validates vulnerability
2023-10-16: Vendor releases patch
2023-10-18: MITRE issues CVE
2025-07-17 - Public Release